Cloud Services :: Cloud 4.0
With experience since 1998, we offer you cloud solutions in our or your own data center, guided by the six criteria of BIO FRIENDLY IT: health, Open Source and Unix, minimizing your IT footprint, best possible IT security, state-of-the-art data security, and maximum independence.
With us, you get everything from a single source: consulting, design, planning, implementation, hosting, and support.
In addition, we also certify systems to BIO FRIENDLY IT so that you can be on the safe side.
VMware vSphere ESXi
Since 2015, we have positive experience with VMware vSphere ESXi, a virtualization platform on the basis of which we offer our customers perfect virtual cloud solutions. In the future, we also plan to use Proxmox.
Linux
We have been working as Linux system administrators, since 1999, with all components, e.g. web servers, databases, mail, DNS and Java/PHP production environments.
BSD Unix
We are FreeBSD, pfSense firewall, VPN and network experts since 2011 and realize any kind of network.
Network Technology
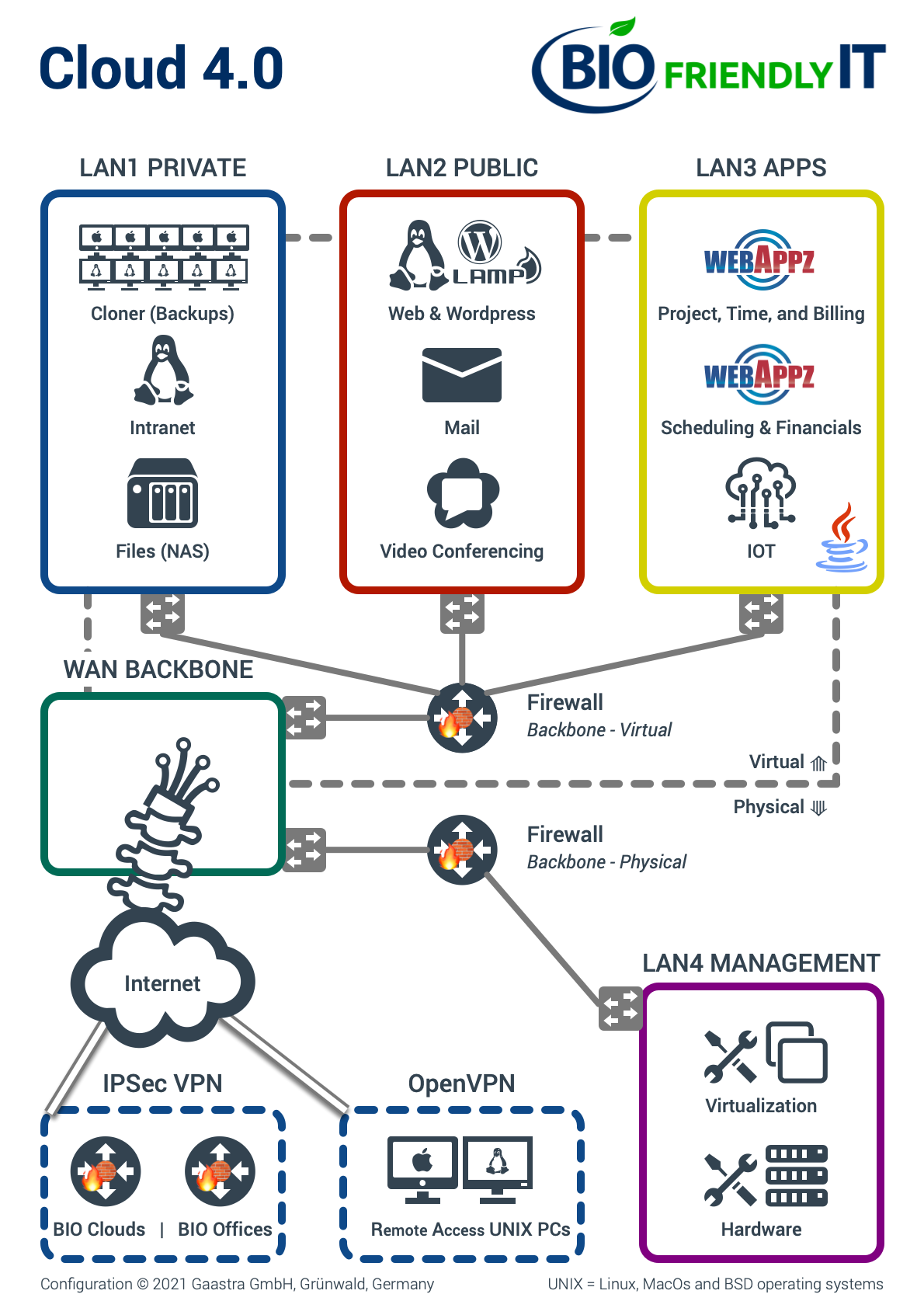
The most basic part of our concept is building your cloud network. We use several so called "virtual subnets" to partition your assets into several network areas with various exactly defined access permissions. This partitioning of the network is precisely controlled by virtual firewalls and virtual switches. This keeps the dangers of a potential attack limited to the respective sub-area. For example, if a video conferencing server were to be attacked, only the "OPEN" network could be accessed through the resulting security hole, while all other parts of the network are secured. (Image below)
Hardware Virtualization
Apart from hardware management, everything in our cloud is virtual, i.e. all networks, switches and all servers! If a hacker were to gain access to the data center, he would still not be able to physically connect to these networks, because there are no technical gateways. Hardware management has its own segregated access with its own IPSec VPN tunnel. Other advantages of virtualization are reliability, power, and space savings.
Optionally, we can configure a second "standby" cluster in another data center - for even greater resilience. If necessary, this would take over virtual network and server functions at another location if the cluster in the first data center fails.
As an energy-saving alternative to a "standby" cluster, we can also equip the cloud hardware with loads of internal failover/redundancy (IT footprint is reduced). A secondary transformer can be used to compensate for the failure of one of the transformers. RAID-6 backed up disks can still be accessed if the main solid state disks fail (which requires daily backup). We also recommend using dual 10Gb fiber connections (on different switches) to the Internet backbone in the data center.
Firewalls
In the past, we always used Cisco's best technologies in the interest of our customers. Since 2011, however, we have been using the open source pfSense Unix system to secure our networks, for (the) Cloud, virtualized or physical. The advantages are: significantly increased security, more functionality, lower hardware costs, less configuration effort, and less power consumption. In the meantime, we try to avoid closed-source firewalls because the code cannot be seen and, consequently, the processes behind them cannot be verified. In our cloud configurations, we use virtual and physical firewalls.
Data Center to Internet Backbone
We place great importance on the most direct connection possible to the main strand ("backbone") of the Internet in order to achieve maximum speed and, incidentally, reduce power consumption and the hardware required. This is achieved by eliminating almost all intermediate stations ("hops"). Fewer intermediate stations means fewer potential security holes and points of failure. The relationship of our "BIO" philosophy to the connection of cloud servers to the backbone of the Internet is again illustrated in the picture.
In our data center, we work together with the best "server hotels" located at the backbone of the Internet, where the main connections from the Internet meet. These connections are Level3, Centurylink, Telia, Core-Backbone and Hofmair. Our data center is located in the east of Munich and meets the latest security requirements. The core features of our data center are:
- BIO FRIENDLY IT Certification
- ISO 27001 Certification
- Two-factor authentication for entry as well as biometric access protection into the colo
- 24/7 video surveillance
- PIN and key-secured modern Rittal and Minkels racks
- Sufficient cooling capacity
- Redundant uninterruptible power supply N+1 including diesel generators as a further protective measure
- Smoke detectors and fire detection with extinguishing system
- Connection realized via BGPv4 uplink for IPv4/IPv6 as a direct LIR member at RIPE
- Connection to Level3/CenturyLink, Telia, core backbone
- Connection to DECIX Frankfurt, ECIX Munich, DECIX Hamburg, DECIX Düsseldorf
- Core network realized with Extreme Networks, Brocade Communications, sub-distribution among others with Juniper
- Greenstream certificate
- 100% Hosted in Germany
We build you the network design with configuration, as well as the setup and configuration of your virtual servers and networks. Subsequently, we take over the complete support. This gives you your own private cloud on our hardware. Alternatively, we can also accommodate your own hardware and care according to our BIO FRIENDLY IT principles.
VPN Tunnel
We configure fixed VPN tunnels (IPSec) between your offices and your private cloud servers. VPN tunnels allow you to transfer your data securely over the "Public Internet". We provide you with the safest tunnels currently available (StrongSwan-Community). Key features of the maximum encryption we use are, for example: IKE V2, AES 256, SHA 512, DH-Group 30 and ESP.
For mobile devices, which in our view are best connected to the Internet via cable, we offer VPN tunnels "on demand" (OpenVPN). This way, your employees can connect their laptop, tablet, or smartphone to your offices or your cloud servers with maximum security. With OpenVPN, we can use similarly strong encryption, for example, AES 256, SHA 512, and D-H 4096 bits.
Private Servers
We can configure private servers that are only accessible from your offices and only for your mobile employees (and IT supervisors) via VPN tunnel. No one else has access to this maximum secured area. Because the risk of fire, theft or other damage is much higher in the office than in our data centers, a data center is the safest place to ensure the protection of your data. We suggest the following services here:
- Cloner Backups: All work devices - Macs, Linux and Windows VMs - are completely mirrored to your private cloud every night. In the event of a device failure, the clone image can be mirrored back from your private cloud to the replacement device in your office or home office in a matter of minutes. Data is strongly secured with 256+ bit encryption in the cloud. Of course, backups and restores are done through our very strongly encrypted VPN tunnels. In addition, we offer "versioned" backups, with a history for a desired period of time.
- Intranet: A server for storing your internal documents within a dynamic "content management" system or Wikipedia system. Optionally, we also offer a system for appointment management ("Calendaring").
- Files: For the storage of important files in their private cloud, we suggest FreeNAS to connect all commercially available operating systems. It includes a web interface, extensive data protection, snapshots, replication and encryption. FreeNAS supports multiple protocols.
Public Servers
Security is extremely important when servers are connected to the public Internet. We therefore usually allow only one port (protocol) from the outside for incoming traffic. For outgoing traffic, only certain update servers are allowed for updates. We host the following, own internet servers for you:
- Webserver (with WordPress): Our goal is always to bring security and speed as close as possible to the theoretical maximum. Our data center is directly connected to the internet "backbone". We perform targeted patches to keep all components at the safest and mostly fastest level. This is one of the unique selling points in our business model. Other advantages: 10 to 100 times faster loading times. Maximum possible SEO ranking due to performance within the European Union. Your open source SSL certificate is updated four times per month and administrator access is restricted by IP or tunnel.
- Mail server: Traditionally, mail traffic between the sending server and receiving server is neither secured nor encrypted. For mails within your own company network we suggest to combine both servers in one package. This prevents anyone from interfering as long as mails are going back and forth between these servers. So, sender domain and recipient domain should both be in your cloud. Of course, the traffic between your mail program and your servers should be encrypted as well.
- Video conferencing server: We host open-source encrypted video conferencing solutions in your own cloud, where no one can join or listen in without an explicit invitation.
- DNS server: "Domain name service" involves converting server and domain namings into associated IP addresses. Despite maximum security on our internal, private networks, on public networks there is always the possibility that your domain provider or non-authorized parties may eavesdrop or even maliciously alter the IP address so that traffic is redirected to a hostile server. We can host the DNS for your private "public" cloud to protect you against such malicious attacks.
.
.

Application Servers
These are servers that serve your operational processes. These servers are accessible from web clients and apps on desktops, laptops and mobile devices. According to the wishes of our customers, we offer a range of options between private and public servers. We prefer Rust, Java and PHP as programming languages and hosting platforms.
BIO 7-Level Data Access Concept (© Gaastra GmbH 2021)
To protect your data, we divide your system into several separate areas. The respective separations of our data access concept can be illustrated by comparing the seven areas in our data center to a hotel. Each level has its own access permissions, its own protections and is mostly inaccessible to the other levels:
- Level 1 - "Your city at the backbone" - Data Center: Only Level 1 employees have access here. Secured against fire, weather, power failures and network failure.
- Level 2 - "Your BIO Aparthotel in the city center" - Colocation Partner: In principle, only Level 2 has access here. Level 3 gets special physical access to its own floor level 3, but only under the escort of an employee of level 2. Also secured against fire, weather, power failures and network failure, especially against "Distributed Denial of Service"(DDoS) attacks.
- Level 3 - "Your premium BIO floor in the hotel" - Physical Server: Only Level 3, i.e. we, Gaastra GmbH, have the management access here via strongly secured VPN tunnels. Although employees of Level 2, theoretically, have the physical access, the floor Level 3 remains protected because these employees do not have appropriate VPN tunnels and passwords.
- Level 4 - "Your wing inside the floor" - Virtual Sub (Sub) Network: From level 4, everything is virtual and there is no physical access. We, Gaastra GmbH, have console access here via our management VPN tunnels. The customer can also get optional access via their own VPN tunnel.
- Level 5 - "Your Apartment" - Virtual Server: As with Level 4, there is only access for Gaastra GmbH and optionally for you, as a customer, again with its own protection. Unlike Level 4, Level 5 is a single server (rather than a network of several servers).
- Level 6 - "The home automation of your apartment" - The backend(s) of the platform: This area is used by the administrator to configure the platform. Here, we protect the access by IP address or VPN tunnel. In addition, the customer needs a "strong" password here. Here, there is only access to level 6 and level 7.
- Level 7 - "The Salon" - The front end(s) of the Platform: Access for end customers is secured via passwords with possible multi-factor authentication (MFA), where access authorization is verified by several independent characteristics (factors). In the case of a website, this access can also take place without authentication. In the case of a public server, we aim that only level 7 is accessible via the public Internet.